River Security | API Security Management Platform (API Bot Defender)
Fully detect all APIs, block every threat. River Security’s API Bot Defender adopts the “ADMP Model”, integrating four core functions – Awareness Perception, Discovery, Monitoring, and Protection – to build a unified API defence system.
It helps enterprises comprehensively manage their API ecosystem and proactively defend against various threats. By leveraging machine learning engines to analyse behavioural patterns, the platform accurately identifies abnormal traffic. Once a threat is detected, the system automatically activates defence mechanisms to ensure zero business interruption.
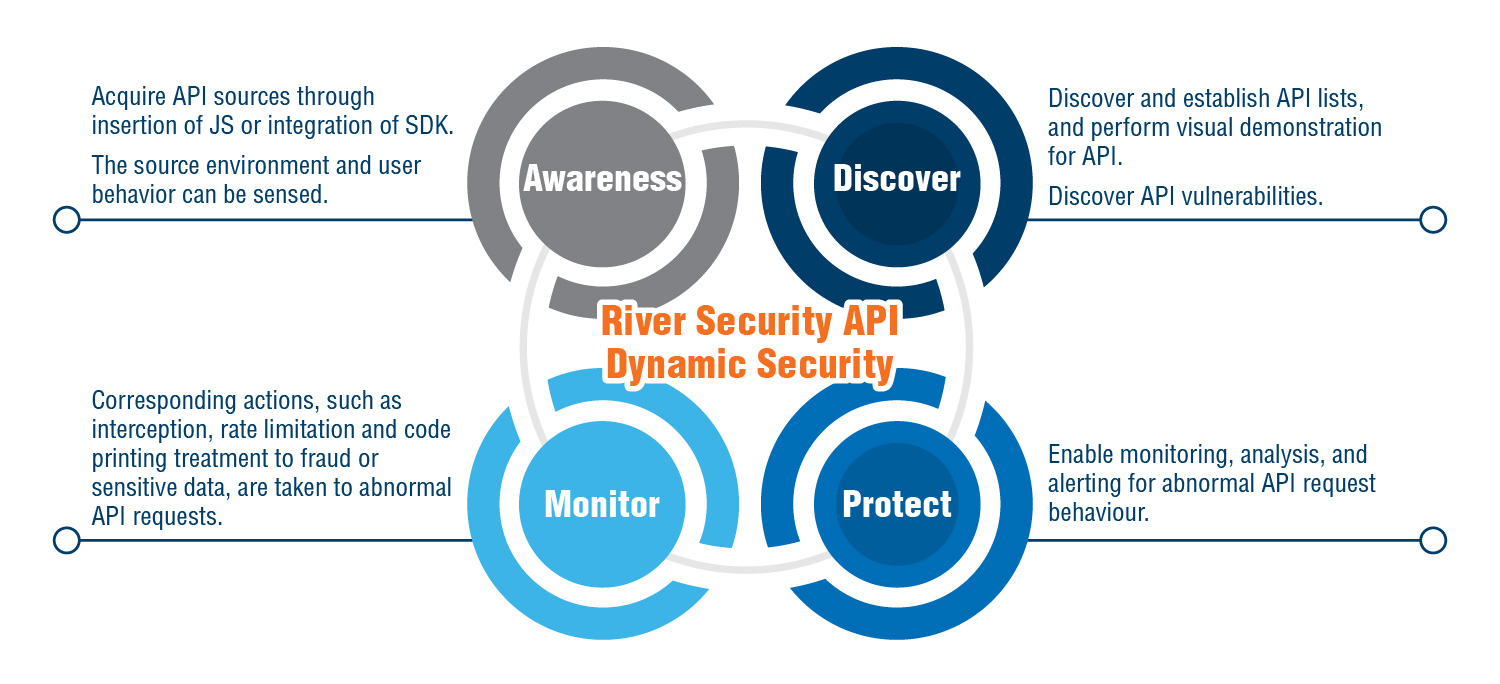
Source: River Security, 2025
Core Functions
-
API Asset Lifecycle Management
- Automatically discover internal and external enterprise API endpoints, supporting multi-dimensional tagging and classification
- One-stop control over the entire API lifecycle
-
API Attack Protection
- Real-time detection and identification of attack behaviours, such as injection attacks or unauthorised access
- Protect APIs and data from malicious crawlers and Challenge Collapsar attacks
-
Sensitive Data Management
- Intelligently identify personal privacy and financial-related data in transit
- Support dynamic masking and real-time blocking to prevent data leakage
-
Traffic Monitoring and Anomaly Analysis
- Establish multi-dimensional API baselines to identify anomalies and malicious activities
- Automatically block threats and mitigate attack impact in real time
-
Unknown API Discovery and Legitimate Call Control
- Automatically compare API gateway registration data to detect unmanaged interfaces
- Prevent unauthorised access through authentication mechanisms, ensuring only legitimate users can access APIs
Technical Advantages of River Security’s API Bot Defender
Multi-Dimensional Awareness
Collect environmental and API account information through JS/SDK embedding and traffic analysis
Precise Identification of API Interfaces
Automatically build API inventories and monitor the status of each interface in real time
Patented Sensitive Data Recognition Algorithm
Significantly improves the speed and accuracy of sensitive data identification, enabling rapid classification and categorisation
Dynamic Access Control Mechanism
Based on machine learning analysis results, automatically execute rate limiting, blocking, or masking policies
River Security’s Success Story Sharing
Customer Pain Points
- API assets are scattered across multiple systems with a lack of centralised oversight.
- Repeatedly targeted by new types of bot attacks, leading to sensitive data leakage.
- Faced strict financial industry compliance review requirements.
Implementation Results
✅Fully integrated and validated 1,500+ API assets, blocked 4,800+ attacks, and protected 730+ high-risk interfaces.
✅Identified 26.6% of sensitive data assets, significantly reducing leakage risks.
✅Met regulatory compliance requirements and comprehensively enhanced corporate data security protection.
✅Identified 26.6% of sensitive data assets, significantly reducing leakage risks.
✅Met regulatory compliance requirements and comprehensively enhanced corporate data security protection.