Under the new Protection of Critical Infrastructures Bill, Critical System Operators (CIOs) must comply with stringent cybersecurity measures and allow regulatory bodies to take action to prevent and address cyber threats. Non-compliance could result in a fine up to $5 million!
Our Critical Infrastructure Solutions
Zero Trust Network Access (ZTNA)
Key Features:
- Context-based access controls
- Integration with VPN, SASE, and multi-factor authentication
- Real-time threat blocking
… Read More Why It Matters:
Eliminate blind trust in your network—protect sensitive data with granular, identity-driven security
Secure Access, No Exceptions
When every connection could be a threat, ZTNA ensures only verified users and devices access critical applications—combining identity verification, VPN, SASE, and 2FA to block unauthorized traffic.Read Less
Network Detection and Response (NDR)
Key Features:
- 24/7 network traffic monitoring
- Impact analysis to prioritize risks
- Automated threat containment
… Read More Why It Matters:
Slash response times and stop attackers before they escalate
Unmask Hidden Threats
Advanced threats often hide in plain sight. NDR uses AI-driven analysis to uncover breaches, map attack paths, and automate rapid responses.Read Less
Privilege Access Management (PAM)
Key Features:
- Credential rotation and least privilege access
- Session recording and audit trails
- Compliance-ready reporting
… Read More Why It Matters:
Prevent insider threats and meet regulatory demands effortlessly
Lock Down High-Risk Accounts
A single compromised credential can cripple your operations. PAM enforces strict controls over privileged accounts.Read Less
Vulnerability Assessment & Penetration Test
Key Features:
- Full-cycle testing: recon, exploitation, and reporting
- Critical infrastructure (CI) – specific risk analysis
… Read More Why It Matters:
Identify and fix vulnerabilities before attackers exploit them
Think Like an Attacker
Go beyond basic scans — simulate real-world attacks with Red Team tactics aligned to the Penetration Testing Execution Standard (PTES).Read Less
Incident Response
Key Features:
- On-site investigation and rapid threat containment
- Post-incident analysis to prevent recurrence
… Read More Why It Matters:
Minimise downtime and reputational impact
When Every Second Counts
Act fast with expert-led containment, forensics, and recovery during breaches.Read Less
Data Availability:
Always-on Access with NextGen-AI Storage
Key Features:
- Self-optimised
- Scalable, cloud-ready architecture
… Read More Why It Matters:
Keep business running, anytime, anywhere
Never Lose Access
AI-powered storage ensures seamless data availability for operations, analytics, and daily workflows.Read Less
Data Resilience & Protection:
Safeguarding Your Data
Key Features:
- Instant recovery from breaches or failures
- Continuous data integrity monitoring
… Read More Why It Matters:
Turn disasters into minor disruptions
Shield Against the Unexpected
Guard against data loss with automated backups, encryption, and fail-safe redundancy.Read Less
Data Portability:
Seamless Data Transfer Across Systems
Key Features:
- API-driven integration and open standards
- Vendor-agnostic migration tools
… Read More Why It Matters:
Future-proof your data strategy without lock-ins
Move Freely, Stay in Control
Break silos in hybrid environments with frictionless data transfer across systems and providers.Read Less
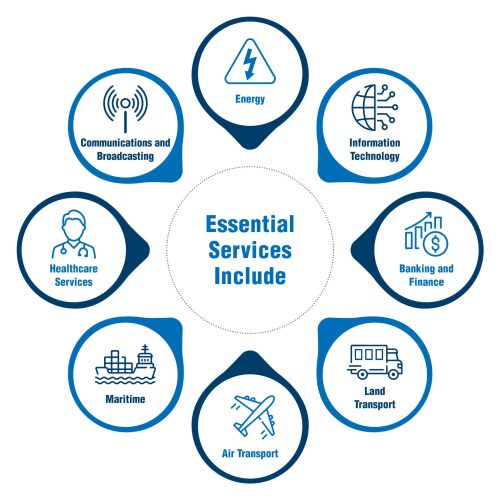
Designated Sectors
Why HKBNES?
Critical Infrastructure Expertise
End-to-End Security
From prevention to recovery, we’ve got you covered