River Security | Data Detection and Response
River Security’s Data Detection and Response (DDR) builds an intelligent line of defence for corporate data, defending against continuously evolving cyber threats.
This system integrates three core defence strategies – proactive risk management, real-time threat detection, and rapid response and recovery – to effectively combat advanced malware, significantly reduce downtime, and achieve minute-level restoration, far exceeding traditional recovery speeds measured in hours.
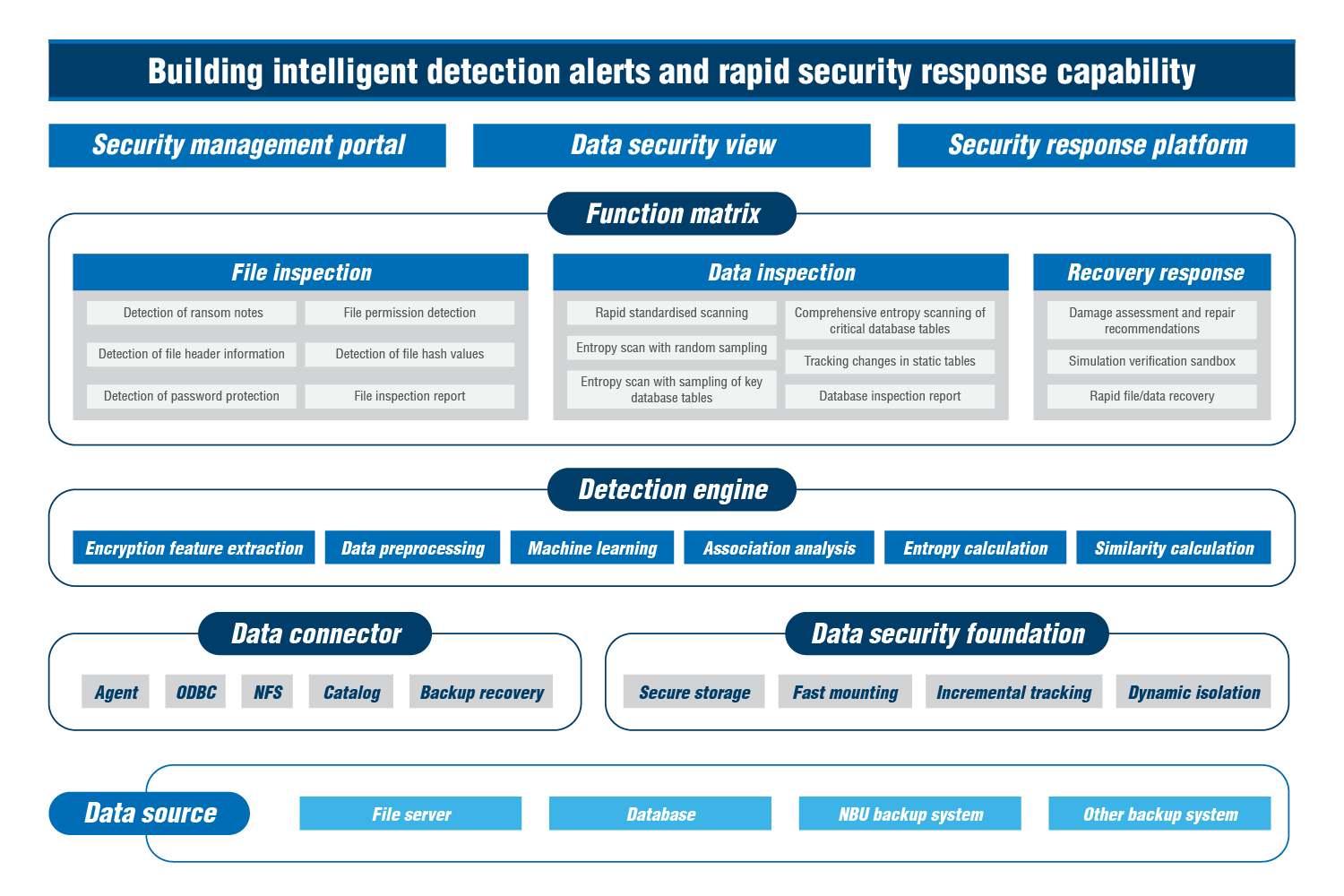
Source: River Security, 2025
Core Functions of River Security DDR
Pre-Attack:
Intelligent Data Asset Identification Engine
- Gain real-time visibility of sensitive data distribution and access rights status.
- Proactively identify risky data (e.g., corrupted or data being encrypted).
During Attack:
Intelligent Threat Detection Engine
- Detect ransomware encryption behaviours and anomalous access activities in real-time.
- Intelligent threat perception to prevent data breaches.
Post-Attack:
Recovery
Intelligent Damage Assessment and Automated Recovery Engine
- Automatically locate compromised data and intelligently match it with the latest clean backup version.
- Immediately restore operations through virtual backup image mounting, minimising business disruption.
Six Key Technical Advantages of River Security DDR
- Complete Asset Transparency Management: Eliminates the “data black box”, enabling organisation-wide visibility.
- Proactive Ransomware Attack Defence: Blocks latent attacks before encryption initiates.
- Data Security Early Warning Mechanism: Provides actionable alerts to prevent data theft.
- Comprehensive Backup Data Protection: Safeguards backups from ransomware, hackers, and internal threats.
- Backup Availability Assurance: Continuously verifies backup data integrity and recoverability.
- Zero Business Interruption Recovery: Achieves minimal downtime through optimised rapid recovery.
River Security’s Success Story Sharing
Customer Pain Points
- Traditional protection could not promptly detect latent ransomware activities.
- Lacked an effective mechanism to verify backup data integrity.
- Slow manual recovery processes posed high risks of business disruption.
- Absence of a proactive threat early-warning system.
Implementation Results
✅Ransomware detection speed increased by 90% compared to traditional solutions.
✅Successfully blocked 98% of potential large-scale data encryption attacks.
✅Reduced business downtime by 95%, achieving minute-level recovery.
✅Successfully blocked 98% of potential large-scale data encryption attacks.
✅Reduced business downtime by 95%, achieving minute-level recovery.